Another way to set up a guest network is by using a secondary router. The secondary router operates in WISP, Repeater, WAP, or a similar mode and rebroadcasts the network with a different SSID. This is popularly done to repurpose old routers as Wi-Fi extenders, but it also works great for setting up a guest Wi-Fi network. Ultimately, what this means for the user is that support for the Guest Networking functionality will depend on the router. But even when supported, the exact steps to use this feature will vary slightly.
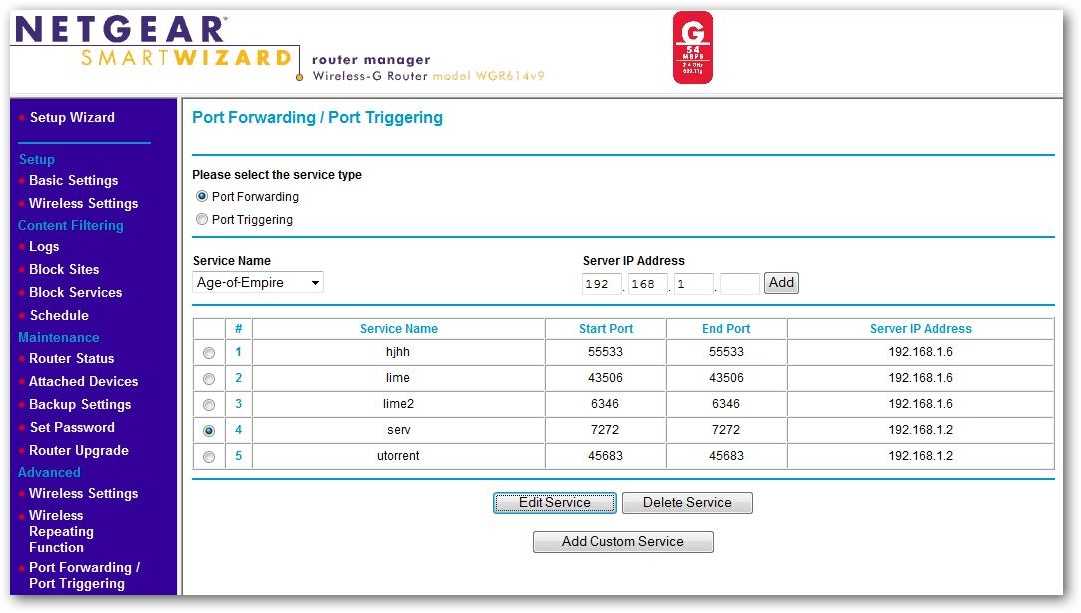
For more flexibility, consider getting a VPS (Virtual Private Server, basically a VM in > More Info the cloud), setting up a VPN between it and your home network and forwarding ports from it. These port forwarding guides should help you configure popular routers to work with No-IP’s Dynamic DNS service. Always remember to consult your router’s user manual or manufacturer’s website for specific instructions on port forwarding, as the process may vary slightly between router models. If you need further assistance or encounter issues while setting up port forwarding, don’t hesitate to Open a Support Ticket with our Customer Support team.
What is Fiber Optics?
A network administrator enters the following commands on the switch SW1. These entries could be predefined (static) to solve the problem with ARP spoofing. Fixing IP spoofing is something out of the control of the end-user, and it can be difficult for sysadmins to handle as well. Overall, you can only mitigate the impact IP spoofing has on your network rather than eradicate it in total. Your IP address is unique to you, as it is for every computer in use today. That address helps to achieve many tasks, such as authentication, encryption, and more. By extension, this makes almost any IP address a target for would-be hackers or criminals.
- IPConfig and IFConfig manage the IP address allocation of a host.
- Above are mentioned some of the methods to deal with several problems related to routers and switches.
- ” Under the SSID selection, choose “YES” and then click on “APPLY” to save your changes.
- NAT and the NAT Forwarding feature are often used in conjunction with each other.
3) If you’re connected to a public wireless network, don’t do any online banking, or make any online purchases. The public network you are connecting to might be a hackers laptop. However, if there is a hacker on your network, they can also answer “I am the real Abe Lincoln”. The unfortunate part is that your computer can’t verify identities, so it just has to assume that the conversation it is beginning to have is with the real Abe Lincoln. It is getting your computer to talk to the hackers computer, instead of to your wireless router. So, this means that you’re the MITM at the moment, and the tool automatically
starts a sniffer for you.
Export Control
Gigabit is the fastest broadband speed range that most homes can currently get, and it’s the target speed for the UK government, which wants 85% of homes to have gigabit internet by the end of 2025. To accelerate customer acquisition before the full buildout, use temporary alternative access options such as leasing capacity from overbuilders or deploying fixed wireless access services in rural areas.



